Sophos Cloud Workload Protection
High impact host and container security. Low impact on performance.
Optimize Workload Protection
Secure Cloud Growth
Cloud or datacenter, host and container. Protect your infrastructure now and as you evolve it with runtime threat detection and prioritized investigations.
Reduce Your Attack Surface
Design cloud environments to meet security best-practice standards, detect workload configuration risk and anomalous activity, and achieve visibility across your whole cloud environment.
Get Performance and Uptime
Flexible, lightweight host and container protection is optimized for performance. Available as an agent or via API to integrate with your security operations, IT, and DevOps processes.
Minimize Time to Detect and Respond
Sophos Cloud Workload Protection provides complete visibility into your host and container workloads, identifying malware, exploits, and anomalous behavior before they get a foothold.
- Extended detection and response (XDR) provides complete visibility of hosts, containers, endpoints, the network and even cloud provider native services
- Cloud-native behavioral and exploit runtime detections identify threats, including container escapes, kernel exploits, and privilege escalation attempts
- Streamlined threat investigation workflows prioritize high-risk incident detections and consolidate connected events to increase efficiency
- Integrated Live Response establishes a secure command line terminal to hosts for remediation

Integrate with Security, IT, and DevOps
Combat threats with actionable host and container runtime visibility and threat detections delivered through the deployment model which best fits your environment.

Single Host Agent
Secure the host and container with a single agent managed from the Sophos Central management console. Easily investigate and respond to behavioral, exploit, and malware threats in one place while increasing IT hygiene with automated detections, intuitive querying, and remote response capabilities.
Integrated Threat Intelligence
Fine-tuned for maximum performance, seamlessly enrich your security operations workflows with an ultra-lightweight Linux sensor providing API integration of host and container behavioral and exploit runtime detections into your existing automation, orchestration, log management, and incident response tooling – available soon.
Get Performance Without Friction
When uptime is your number one requirement, security tools must be lightweight and integrate into your DevSecOps workflows to prevent risk and optimize application performance.
Optimized for Linux
Identify sophisticated Linux security incidents as they happen without deploying a kernel module, which can introduce security risk through third-party code and require you to recompile the kernel when each new update is pushed.
Designed to Avoid disruption
Avoid costly downtime, overloaded hosts, or stability snafus caused by traditional security tools with a single agent with optimized resource limits (including CPU, memory, and data collection limits).
Automate Your Cloud Security Checklist
Design your cloud environments to meet security best-practice standards with the visibility and tools to maintain them using integrated Sophos Cloud Optix Standard capabilities.

- Proactively identify unsanctioned activity and misconfigurations across Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP)
- Continuously discover cloud resources with detailed inventory and visibility of Sophos host protection and Sophos Firewall deployments
- Automatically overlay security best practice standards to detect gaps in posture as well as identify quick wins and critical issues
- Detect high-risk anomalies in user IAM role behavior, pinpointing unusual access patterns, locations, and malicious behaviors quickly to prevent a breach
Get Flexible Host and Container Protection
As your organization expands from on-premises or data center to hybrid and multi-cloud environments, Sophos protects your infrastructure and data across deployment and computing models.

Linux Security
Detection and resilience for Linux systems in any environment, including container runtimes such as Docker, containerd, and CRI-O. Our detection is crafted with the threat models of cloud-native systems in mind.

Windows Security
Secure your Windows hosts and remote workers against ransomware, exploits and never-before-seen threats, control applications, lockdown good configurations, and monitor changes to critical system files.

Hybrid and Multi-Cloud
Secure applications and data across your hybrid cloud footprint from a single console. The flexible agent runs on-premises, in data centers, hybrid and multi-cloud environments including AWS, Azure, GCP and Oracle Cloud.
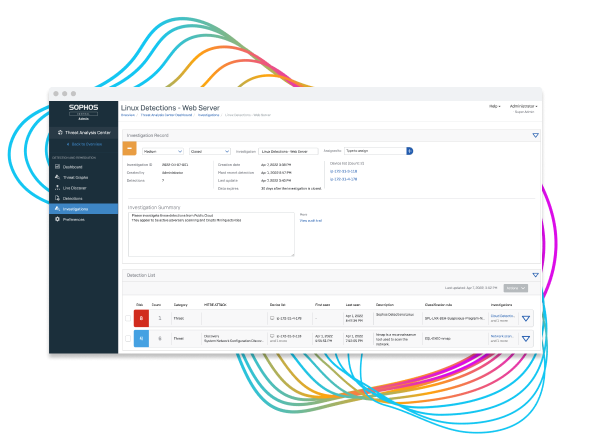
Resolve Security Incidents Faster
The intuitive detection dashboard makes it easy to increase incident response efficiency. Host and container threat detection automatically converted into an investigation, with an AI-prioritized risk score for each detection. Scores are then color-coded and mapped against the MITRE ATT@CK framework, enabling an analyst to quickly identify where they should focus, or not.
Detections include: malware targeting Linux, memory corruption, new file behavior, unusual application behavior, suspicious interactive shell, container escapes, kernel and userland backdoors, privileged file operations, network discovery, lateral movement, process injection, system discovery, scheduled task changes, complier usage, privileged command usage, and risky developer activity.

Hunt Threats and Harden IT Ops
Get information that matters to you – fast. Choose from a library of pre-written templates for threat hunting and IT operations scenarios, customize them, or write your own. You have access to live data, up-to 90 days on-disk and 30 days of data stored in the Sophos Data Lake so you’re covered for every scenario.
Take the Weight of Cloud Security off Your Shoulders
Our flexible approach to cybersecurity deployment and management means optimizing security, keeping data secure and private while blocking active threats are goals you can easily achieve.
- Your organization’s team can deploy and manage Sophos protection from a single unified console
- Sophos can connect you with an experienced Sophos Managed Security Partner
- Sophos own Professional Services Team can help with initial deployment

Respond to Security Incidents at 3 a.m.
Sophos Managed Threat Response, the Sophos MDR service, can work in partnership with your team and Sophos MSP, monitoring your environment 24/7/365, and proactively hunting for and remediating threats on your behalf.
- Threat Hunting: Proactive threat hunting by our elite team of threat analysts. Determining the potential impact and context of threats to your business
- Response: Initiates actions to remotely disrupt, contain and neutralize threats on your behalf to stop even the most sophisticated threats
- Continuous Improvement: Get actionable advice for addressing the root cause of recurring incidents to stop them from occurring again


Hybrid Cloud Security Trusted by Millions
Sophos is trusted by millions to provide intuitive and incredibly broad visibility and protection. Available in a single unified management console, Sophos Central. Sophos combines Cloud Workload and server protection with endpoint and mobile device security, firewall, zero trust network access, secure email and more. Now available in AWS Marketplace to help streamline cloud security procurement, while counting towards any cloud provider consumption commitments your organization already has in place.
Downloads
Videos
Sophos News
- Sophos ranked #1 overall for Firewall, MDR, and EDR in the G2 Winter 2025 Reports
- Sophos XDR: New generative AI functionality and case investigation enhancements
- Cybersecurity Awareness Month: A timely reminder to review your security posture
- Sophos named a Leader in the 2024 Gartner®️ Magic Quadrant™️ for Endpoint Protection Platforms