Synchronized Security
Synchronized Security is the world’s first – and best – cybersecurity system.
Cybersecurity Delivered
Synchronized Security is the world’s first – and best – cybersecurity system. Endpoint, network, mobile, Wi-Fi, email, all sharing information in real time and responding automatically to incidents:
- Isolate infected endpoints, blocking lateral movement
- Restrict Wi-Fi for non-compliant mobile devices
- Scan endpoints on detection of compromised mailboxes
- Identify all apps on the network
And with everything controlled through the Sophos Central cloud-based security platform, management is a breeze.
Think You Know Ransomware?
A gripping documentary that delves into the alarming realities of ransomware, revealing the far-reaching consequences that affect both business owners and society at large.
Reduce cyber risk
Automated incident response minimizes exposure to security threats, while cross-product data sharing reveals previously hidden risks.
Enhance cross-estate visibility
Get previously unseen insights into network traffic and users, while viewing and controlling all your security in one place.
Increase Return on Investment
Scale your security without scaling your resources by consolidating all your protection in a single cloud-based platform.
Hear What Our Customers Say
 Why We Use Sophos Synchronized Security
Why We Use Sophos Synchronized Security
It's saved us a lot of time, a lot of money, and a lot of heartache.
Zero Touch Response
See how Sophos products work together to slash your exposure to threats while freeing up IT.
 Sophos XG Firewall Synchronized App Control
Sophos XG Firewall Synchronized App Control
Identify all apps on the network
On average, 45% of network traffic can’t be identified. See how Sophos Firewall and Sophos Endpoint work together to identify all network traffic, revealing hidden risks and unknown threats.
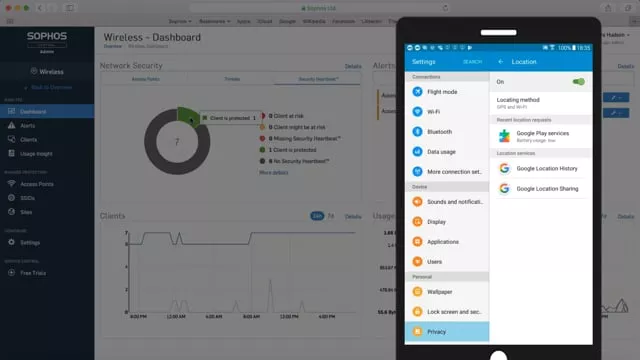 Synchronized Security: Sophos Wireless and Sophos Mobile
Synchronized Security: Sophos Wireless and Sophos Mobile
Restrict Wi-Fi for non-compliant mobile devices
See how Sophos Mobile and Sophos Wireless work together to reduce risk from non-compliant devices, and how you can track it all in real time.
 Synchronized Security Stops Advanced Threats
Synchronized Security Stops Advanced Threats
Isolate infected endpoints
See how Sophos Endpoint and Sophos Firewall systematically work together to stop a ransomware attack.
How to Get Synchronized Security
To enable Synchronized Security, all you need is two or more Sophos products that work together. At least one product must be managed through the Sophos Central management platform. And if you’re already a Sophos customer, you’re already halfway there.
You do not need any additional subscriptions to enable Synchronized Security
Intercept X and Sophos Firewall
Intercept X and Sophos Firewall
HOW THEY WORK TOGETHER
-
Automatically block compromised devices from accessing corporate data
-
Identify unclassified apps and processes that are using bandwidth
-
Block worm-like lateral movement, automatically isolating infected machines
-
Automatically generate RCAs for threats blocked at both the endpoint and the firewall (requires EDR)
-
Find the source (user, device) of bad traffic in the network
-
Identify what is causing malicious traffic from a device
-
Quickly classify and block all undesirable apps using up bandwidth
-
Rate-limit certain apps on the network
(includes all Central-managed endpoint protection subscriptions)
Intercept X for Server and Sophos Firewall
Intercept X for Server and Sophos Firewall
HOW THEY WORK TOGETHER
-
Block compromised devices from accessing corporate data with one click
-
Identify unclassified apps and processes that are using bandwidth
-
Block worm-like lateral movement, isolating infected machines with one click
-
Find the source (user, device) of bad traffic in the network
-
Quickly classify and block all undesirable apps using up bandwidth
-
Rate-limit certain apps on the network
-
Protect servers from other compromised machines on the network
-
Identify what is causing malicious traffic from a device
(includes all Central-managed server protection subscriptions)
Intercept X and Sophos Email
Intercept X and Sophos Email
HOW THEY WORK TOGETHER
-
Automatically check whether malware has been installed on devices with compromised mailboxes
(includes all Central-managed endpoint and email protection subscriptions)
How to Buy
With Synchronized Security, you enjoy flexible implementation options, making it as easy as possible to get started.
Start with one product, add others later
You’ll get the benefits of Synchronized Security as soon as you add the additional products, and in the meantime will enjoy great protection from your first product.
Deploy multiple products at the same time
You can still add additional products at a later date to further extend your Synchronized Security system.
